BLUE CHIP
CYBERSECURITY
SOLUTIONS
BLTS continually surveys the cyber intelligence market for innovative and upcoming technologies to confidently protect our clients from cyberattacks.

THREAT INTELLIGENCE & ATTRIBUTION
UNPARALLELED STRATEGIC INTELLIGENCE
Optimize strategic, operational and tactical decision making with best-in-class threat intelligence.
The first line of defense shouldn’t be your infrastructure. Gain unparalleled insight into adversaries targeting your organization, partners, or clients with high-fidelity threat intelligence.
Prevent, deter and defeat attacks by analyzing and attributing cyberattacks, hunting for threats, and fortifying network infrastructure.
THREAT HUNTING FRAMEWORK
ADVERSARY-CENTRIC DETECTION OF TARGETED ATTACKS AND UNKNOWN THREATS FOR IT AND OT ENVIRONMENTS.
Threat Hunting Framework (THF) is your local center for research, detection, and response. Capabilities include:
-
Management of complex incidents
-
Malware detonation and analysis
-
Collaboration with experts
-
Proactive threat hunting
-
Access to threat intelligence
-
Unified security solution for IT+OT


DIGITAL RISK PROTECTION
AI-DRIVEN DIGITAL RISK IDENTIFICATION AND MITIGATION PLATFORM
Artificial intelligence that manages your risk exposure.
-
Identifies illegitimate use of digital assets
-
Classifies and scores the detected violations
-
Prioritizes and initiates appropriate takedown tactics
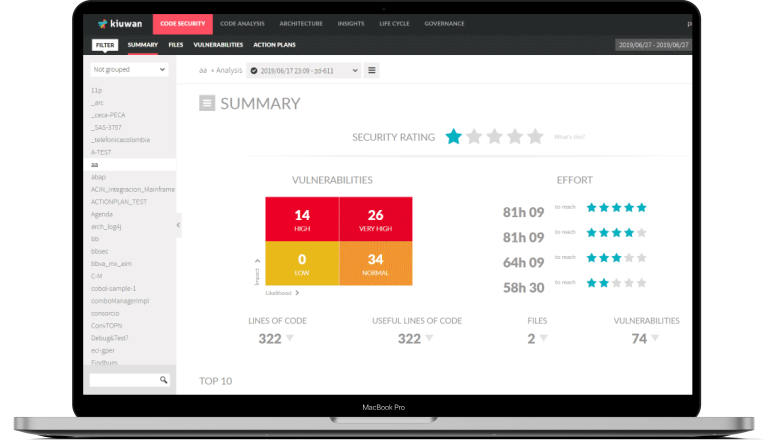
DATA & CODE PROTECTION
SECURE YOUR CODE AT EVERY STAGE.
Automatically scan your code to identify and remediate vulnerabilities. Compliant with the most stringent security standards and integrates directly with leading DevOps tools across the SDLC.
-
Get Rapid Results
-
Make Informed Decisions
-
Customize to your needs

CLOUD PROTECTION
COMPREHENSIVE CLOUD SECURITY MANAGEMENT PLATFORM.
Secure the entire cloud lifecycle across infrastructure, applications, data and entitlements using a natively built unified security platform.
-
Cloud Security Posture Management
-
Cloud Infrastructure Entitlement Management
-
Cloud Compliance
PRIVILEGES & APPLICATION CONTROL
TAKE CONTROL OF PRIVILEGED ACCESS TO YOUR ENVIRONMENT.
Implement the most strict and complex controls on access to privileged credentials in an automated and centralized manner, protecting your IT infrastructure from data breaches and potential compliance breaches.
-
Protect your business from insider threats and critical data theft
-
Monitor and record activities performed during access sessions
-
Streamlined audit reporting from a central audit data repository
-
Automatic reset of passwords or based on an established schedule
-
Securely encrypted password management
-
Control of privilege misuse in your company


ANTI-PIRACY
SMART PROTECTION OF YOUR DIGITAL CONTENT.
Protect your brand against pirated usage and unauthorized distribution of unique digital content.
-
Cloud Security Posture Management
-
Cloud Infrastructure Entitlement Management
-
Cloud Compliance
